Security
When it comes to containers, their convenience and efficiency come with a unique set of security considerations, distinct from those of traditional virtual machines (VMs). Here’s why security in the container world needs special attention:
Shared Kernel Risks:
Unlike VMs, all containers on a system share the same operating system kernel. This is efficient but risky. If a container has too much access, it could potentially control or damage the entire system, such as by killing processes or changing network settings. This is a crucial difference to remember, as it highlights why container isolation is not as strong as the isolation in VMs.
Privilege Problems:
A common security issue with containers is running them with too many privileges, often as the root user. This can open the door to various security breaches, as a compromised container could lead to broader system compromises.
Risks with Public Images:
Using public container images, like those from Docker Hub or Quay, introduces another security concern. While these repositories offer a vast selection of readily available images, there’s a risk that some may have been tampered with to include harmful software.
Building Secure Container Images:
Ensuring the security of container images involves vigilance and a proactive approach. For instance, avoiding unnecessary privileges and carefully inspecting public images for security issues are key steps. Resources like Sysdig’s blog provide detailed guidance on securing container images.
The 4C's of Cloud Native Security:
Security isn’t just about the containers themselves but involves multiple layers:
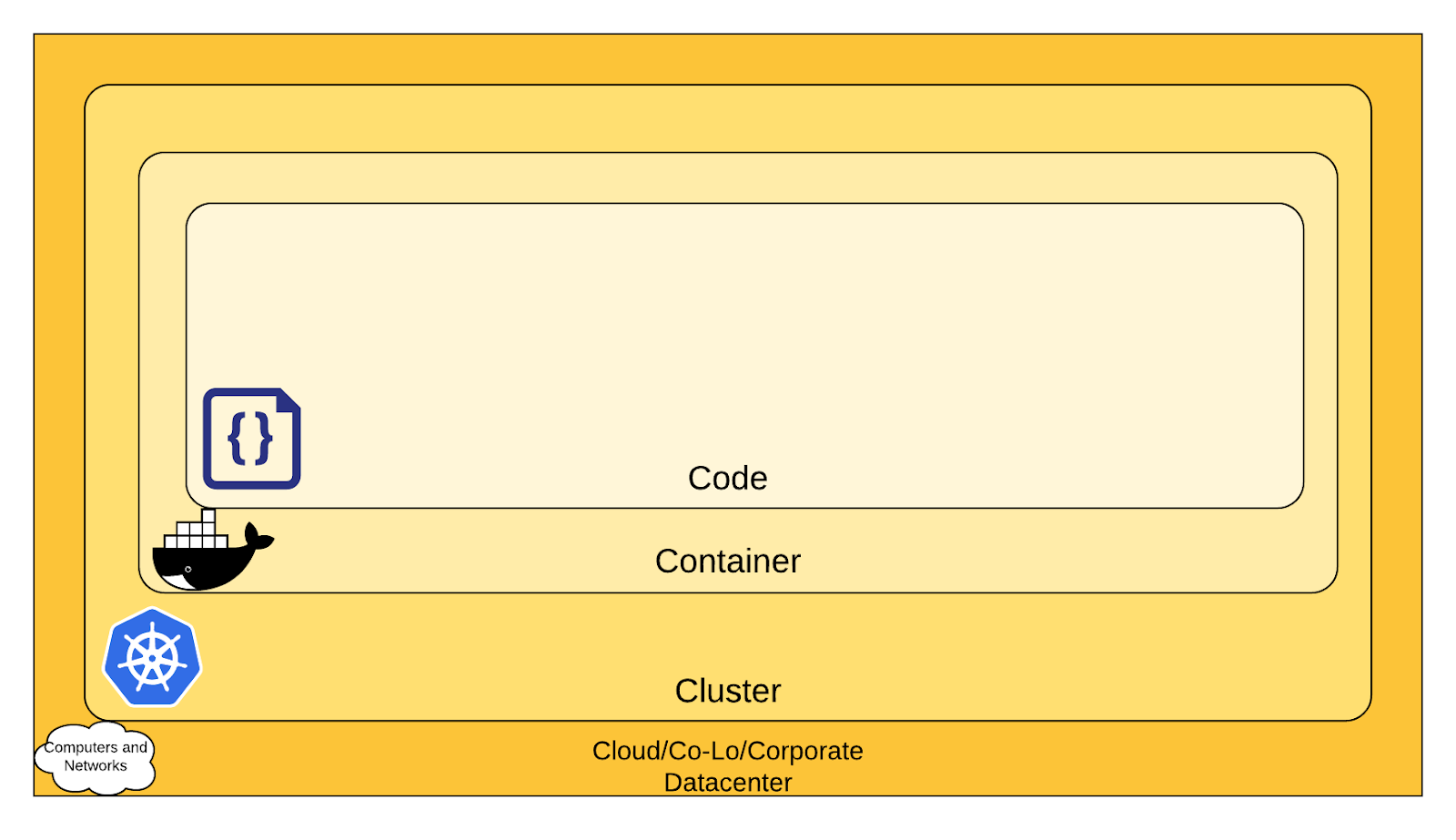
Code: Security at the application code level.
Container: Focusing on the container, its runtime, and the software stack within.
Cluster: The orchestration level, such as Kubernetes, managing how containers are deployed and interact.
Cloud: The infrastructure (servers, networks) on which everything runs.
This layered approach means that securing one layer helps protect the others, but it’s vital to address each layer specifically. Kubernetes documentation, for instance, offers insights into securing these layers in a cloud-native environment.
Container security is a complex but manageable challenge. It requires understanding the unique aspects of container technology, like shared kernels and the risks of running containers as root. By focusing on the security of each layer from the code to the infrastructure and being cautious with public images, you can build a strong defense for your containerized applications.
Last updated