Networking Objects
Kubernetes networking simplifies the complex task of managing network configurations for a potentially large number of Pods. It achieves this through the use of Service and Ingress objects, which abstract and define networking within the cluster. Let's explore these core networking objects and their types, focusing on how they facilitate communication and expose applications.
Kubernetes Service Types
1. ClusterIP
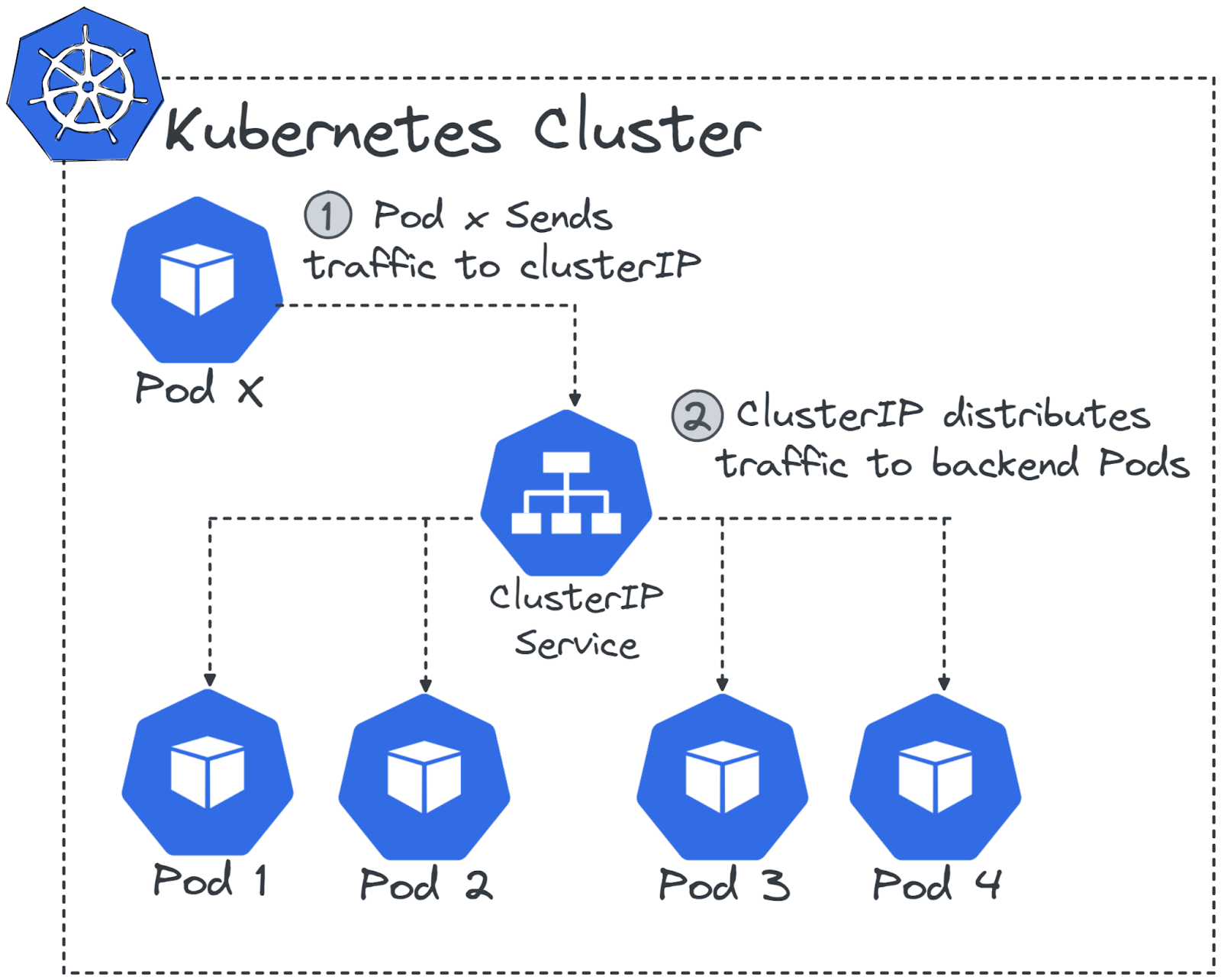
What It Is: The default and most common type of Service, providing a virtual internal IP address for a group of Pods. It enables internal communication within the cluster, acting as an internal load balancer.
Use Case: Ideal for applications that need to be accessible only within the cluster.
2. NodePort
What It Is: Extends ClusterIP by opening a specific port on all Nodes’ IPs, allowing external traffic to reach the Service, routed through the ClusterIP.
Use Case: Useful for exposing a service on a fixed port across all nodes, often used for initial development exposure or small-scale environments.
3. LoadBalancer
What It Is: Builds on NodePort by integrating with cloud providers’ load balancers, automatically creating an external load balancer that directs traffic to the NodePort across your nodes.
Use Case: Perfect for production environments where external access to services is needed with the added benefit of using cloud providers' native load balancing features.
4. ExternalName
What It Is: A special service type that creates a DNS alias, not actually routing any traffic but providing a way to refer to external services.
Use Case: Useful for integrating external services, like a database outside of Kubernetes, into your internal DNS structure without actual routing.
5. Headless Services
What It Is: A Service without a single virtual IP, directly exposing the Pod IPs to allow for direct access without load balancing or proxying through Kubernetes.
Use Case: Ideal for when you need to communicate directly with specific Pods or when using custom service discovery mechanisms.
Ingress : Managing External Access
Ingress objects allow more fine-grained control over external access to services within the cluster, offering features like SSL/TLS termination, virtual hosting based on domain names, and path-based routing.
Use Cases: Ideal for defining complex routing rules to services, such as directing different paths on a domain to different services within the cluster.
Network Policies : The Kubernetes Firewall
Network Policies act as a firewall for Pods within a Kubernetes cluster, allowing you to control which Pods can communicate with each other and with other network endpoints.
Use Cases: Essential for securing your cluster by limiting connections to and from Pods, enforcing isolation between different parts of your application or between different teams' resources.
To practically understand how to expose applications using Services and manage traffic with Ingress objects, consider exploring the interactive tutorials available in the Kubernetes documentation. These tutorials provide hands-on experience, reinforcing the concepts discussed here.
Last updated